Kaspersky cybersecurity experts have conducted new research into an unusual way to steal passwords using a thermal camera. This time, in addition to ATMs, they also focused on smartphones and computer keyboards.

Thermal imaging attacks have been on researchers’ radar for more than 15 years. One of the first studies in this field deals with the most common scenario in the real world – ATM attack. However, it turns out that smartphones and keyboards can also be vulnerable to thermal attacks.
Scientists from the University of Glasgow in Scotland developed the system ThermoSureWhich uses a thermal imaging camera to identify keys touched by an ATM user or computer. Then select the device used keys Guess the passwords entered on the keyboards for both PC and ATM machinesEven after a minute of typing it.

Criminals can steal ATM password
In order to test the system, the researchers did 1500 thermal images of newly used keyboards at different angles. The team then used an AI model to efficiently read the images and make informed guesses about passwords from the heat signature cues.
According to scientists As much as 86 percent of the passwords were guessed correctly Within twenty seconds of writing it. Over time – between using the keyboard and taking a picture – the effectiveness of sequence decoding decreased, reaching 76%. After 30 seconds, 62 percent. After 60 seconds.
Before Taking a PIN to an ATM, However, You Can Avoid It. This is a new mission The safety principle that everyone should follow. Just enter it using the item you It will not emit heat – As is the custom of human hands. you can do it Use the keys – After all, everyone usually has them – or a bigger coin. It is a recommended solution for summer and spring. After all, in the fall and winter you can do this Use appropriately thick gloves that reduce heat transfer through your fingers.
Thermovision and smartphones
Company researchers Kaspersky We believe – as in the case of ATMs – The success of a smartphone attack depends on how quickly the thermal image is captured after entering a PIN or secret combination. Taking a photo is more difficult in this case because unlike an ATM, people hold their photos smart phones with me. Either way, you can imagine a situation where someone in a crowd (eg on a bus) takes a picture like this.

A 2017 study cited by experts demonstrated that data analysis techniques had improved and the overall success rate was higher than in the 2011 ATM trials. Up to 89 percent PIN codes were successfully obtained thanks to the timely use of thermal imaging.

PINs and patterns for unlocking smartphones and their thermal effects.
As much as 78 percent were cracked when the photo was taken 30 seconds after unlocking the phone, and 22 percent when researchers waited 60 seconds. By the way, pattern locks are difficult to identify using this method. However, there is another problem with them. In 2010, these combinations turned out to be fairly easy to guess by fingerprints left on the screen, which stay there much longer than thermal fingerprints.
Thermovision and keyboard
Researchers at the University of Glasgow in Scotland, to truly test the possibilities of thermal espionage, tried it Alphanumeric passwords are entered on a real keyboard.

Heat effects from pressing keys on a computer keyboard.
In this study – as in other studies – The reliability of password recovery after the specified time has been tested: Thermal discharge was performed at intervals of 20, 30 and 60 s. There is a new variable in the form of password length, which can be any. Most importantly, the researchers applied machine learning algorithms. Algorithms trained on hundreds of keyboard images paired with known combinations have shown excellent results in password recovery.

Surprisingly, in half of the cases it was possible to recover even a 16-character long password.
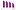
The method of password retrieval depends on the time between input and capture, as well as the length of the password.
There were also some unexpected discoveries. The effectiveness of the method depends on the type of plastic Some heat up less than others. It is also important that the keyboard is backlit. In general, any external heating of the buttons – whether it’s from the built-in LEDs or from a processor located under the keyboard in a laptop – destroys the thermal trace. Another note – the faster the password is entered, the less likely it will be revealed in the thermal imaging.
Konrad Siwick, journalist at dobreprogramy.pl

“Prone to fits of apathy. Introvert. Award-winning internet evangelist. Extreme beer expert.”

![What a scene. This is how Barcelona players welcomed Lewandowski [WIDEO] football What a scene. This is how Barcelona players welcomed Lewandowski [WIDEO] football](https://www.moviesonline.ca/wp-content/uploads/2022/11/What-a-scene-This-is-how-Barcelona-players-welcomed-Lewandowski.jpg)







